Clickjacking: Be Aware of clicking, What is clickjacking
Published on: owasp.com
source: Click here
Clickjacking, a subtype of UI redressing, is a harmful technique in which a web user is tricked
into engaging (usually by clicking) with something other than what the user expects to connect with.
This type of attack, alone or in combination with other assaults, has the potential to send unwanted orders or divulge personal
information while the victim interacts with seemingly harmless online pages. Jeremiah Grossman and Robert Hansen created the term
"clickjacking" in 2008.
A clickjacking attack takes advantage of seemingly harmless HTML and JavaScript elements to force the victim to execute unwanted activities,
such as clicking an invisible button that performs an undesirable operation. This is a client-side security vulnerability that affects a wide
range of browsers and platforms.
Clickjacking: How clickjacking works ?
Published on: medium.com and csp.com
source: (XFO) Click here and (CSP) Click here
By default, the internet is highly open. Your website or critical online application will "agree"
to be embedded in any other website in the globe. Furthermore, the authenticated cookies will be included in the
requests to your server. You can explicitly limit the ability to embed your site the CSP frame-ancestors and/or the legacy X-Frame-Options.
When you configure these HTTP Response Security Headers in web page responses the browsers will
BLOCK the loading of the content in the iframe - even if it was approved and provided by the server.
What is X-Frame-Options(xfo) ?
The X-Frame-Options (XFO) HTTP response header specifies whether a browser should be allowed to render a web page in a frame or
an iframe. It is a security feature intended to avoid clickjacking attacks, in which an attacker mislead a user into clicking on
something other than what the user perceives, perhaps leading to unexpected consequences.
X-Frame-Options header can have three possible values:
1. DENY: This value prevents any domain from framing the web page. It effectively denies all attempts to load the page in a frame.
Example: X-Frame-Options: DENY
2. SAMEORIGIN: This value allows the page to be framed only by pages from the same origin (i.e., the same domain). It provides a good balance between security and functionality.
Example: X-Frame-Options: SAMEORIGIN
3. ALLOW-FROM uri: This value allows the page to be framed by the specified URI. It provides more flexibility in terms of framing permissions.
Example: X-Frame-Options: ALLOW-FROM https://example.com
What is Content Security Policy(CSP) ?
The name of an HTTP response header used by current browsers to improve the security of the document (or web page) is Content-Security-Policy.
The Content-Security-Policy header lets you to specify which resources (such as JavaScript, CSS, Images, and so on) can be loaded and from which
URLs they can be loaded.The term Content Security Policy is often abbreviated as CSP. CSP was first designed to reduce the attack surface of Cross
Site Scripting (XSS) attacks, later versions of the spec also protect against other forms of attack such as ClickJacking.
Concepts of Content Security Policy include:
1. Default-src : The default-src directive defines the default policy for fetching resources such as JavaScript, Images, CSS, Fonts, AJAX requests, Frames, HTML5 Media. Not all directives fallback to default-src.
Example: default-src 'self' example.com ;
2. Script-src : Defines valid sources of Javascript.
Example: script-src 'self' js.example.com ;
3. Style-src : Defines valid sources of stylesheets or CSS.
Example: style-src 'self' css.example.com ;
4. Img-src : Defines valid sources of images.
Example: img-src 'self' example.com ;
5. Connect-src :Applies to XMLHttpRequest (AJAX), WebSocket, fetch(), a ping or EventSource. If not allowed the browser emulates a 400 HTTP status code.
Example: connect-src 'self' ;
6. Frame-src : Defines valid sources for loading frames. In CSP Level 2 frame-src was deprecated in favor of the child-src directive. CSP Level 3, has undeprecated frame-src and it will continue to defer to child-src if not present.
Example: frame-src 'self' ;
Clickjacking: Example of the attack
Published on: imperva.com
source: Click here
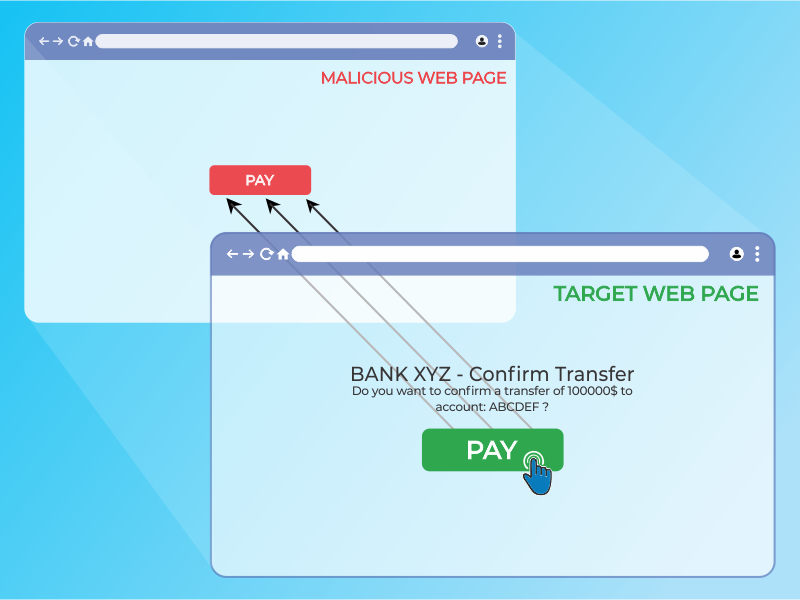
1. The attacker creates an attractive page which promises to give the user a free trip to Tahiti.
2. In the background the attacker checks if the user is logged into his banking site and if so,
loads the screen that enables transfer of funds, using query parameters to insert the attacker’s bank details into the form.
3. The bank transfer page is displayed in an invisible iframe above the free gift page, with the “Confirm Transfer” button exactly
aligned over the “Receive Gift” button visible to the user.
4. The user visits the page and clicks the “Book My Free Trip” button.
5. In reality the user is clicking on the invisible iframe, and has clicked the “Confirm Transfer” button. Funds are transferred to the attacker.
6. The user is redirected to a page with information about the free gift (not knowing what happened in the background).
Clickjacking: Cases of clickjacking
Published on: The Hacker News
source: Click here
Cases 1: New unpatched bug could let attackers steal money from PayPal users
A security researcher claims to have discovered an unpatched vulnerability in PayPal's money transfer service that could
allow attackers to trick victims into unknowingly completing attacker-directed transactions with a single click.

Clickjacking, also called UI redressing, refers to a technique wherein an unwitting user is tricked
into clicking seemingly innocuous webpage elements like buttons with the goal of downloading malware, redirecting
to malicious websites, or disclose sensitive information.
This is typically achieved by displaying an invisible page or HTML element on top of the visible page,
resulting in a scenario where users are fooled into thinking that they are clicking the legitimate page when they
are in fact clicking the rogue element overlaid atop it.
"Thus, the attacker is 'hijacking' clicks meant for [the legitimate] page and routing them to another page,
most likely owned by another application, domain, or both," security researcher h4x0r_dz wrote in a post documenting the findings.
"This endpoint is designed for Billing Agreements and it should accept only billingAgreementToken," the researcher explained.
"But during my deep testing, I found that we can pass another token type, and this leads to stealing money from [a] victim's PayPal account."
This means that an adversary could embed the aforementioned endpoint inside an iframe, causing a victim already logged in a web browser
to transfer funds to an attacker-controlled PayPal account simply on the click of a button.
Even more concerningly, the attack could have had disastrous consequences in online portals that integrate with PayPal for checkouts,
enabling the malicious actor to deduct arbitrary amounts from users' PayPal accounts.
"There are online services that let you add balance using PayPal to your account," h4x0r_dz said.
"I can use the same exploit and force the user to add money to my account, or I can exploit this bug and let the victim create/pay Netflix account for me!"
Cases 2: Fake ClickJacking Bug Bounty Reports the Key Facts
What are clickjacking bug bounty reports?
If we start by breaking up the term into its component parts, a bug bounty is a program offered by an organization, in which individuals are rewarded for
finding and reporting software bugs. These programs are often used by companies as a cost-effective way to find and fix software vulnerabilities, thereby improving the security
of their products. They also help to build goodwill with the security community.
For the bounty hunters (or white hat hackers), they have an opportunity to earn money and recognition for their skills.Clickjacking is a malicious technique
used to trick users into clicking on something that they think is safe, but is actually harmful. For example, a hacker could create a fake button that looks like the "like"
button on a social media site. When users click on it, they may unknowingly like a page or post harmful content. While this may seem like a harmless prank, clickjacking can be used
for more malicious purposes, such as infecting a user's computer with malware or stealing sensitive information.
Given the potential damage, clickjacking can cause, big bounties that report cases of it can be very beneficial to an organization.

As a bug bounty report can bring financial benefits to both the bounty hunter and the organization, the former will often not wait for an invite to hunt for bugs
and will take a more proactive approach. This means you could be sent bounty reports even if you don't have a formal bug bounty program in place. This practice –
where a report comes unsolicited with a request for money – is often referred to as a "beg bounty".
There is a growing trend in fake bug bounty reports because individuals are using scanning tools to generate "issues" and then flagging them to as many organizations
as possible without consideration of the real risk.
While some will look fake, other reports may be sophisticated enough to con an organization out of thousands of dollars. And by falling victim, you don't just pay a
reward that is undeserved; you also show the bounty hunter that you have limited security expertise – a weakness they are highly likely to come back and exploit.
Of course, shutting the doors and ignoring all bug bounty reports is not the answer. There are genuinely good people out there who are trying to help, and their discovery may just
save your business a lot of grief and expense.
Cases 3: Dozens of Android Apps for Kids on Google Play Store Caught in Ad Fraud Scheme
A security researcher claims to have discovered an unpatched vulnerability in PayPal's money transfer service that could
allow attackers to trick victims into unknowingly completing attacker-directed transactions with a single click.
More than 50 Android apps on the Google Play Store—most of which were designed for kids and had racked up almost 1 million
downloads between them—have been caught using a new trick to secretly click on ads without the knowledge of smartphone users.
Dubbed "Tekya," the malware in the apps imitated users' actions to click ads from advertising networks such as Google's AdMob, AppLovin', Facebook, and Unity, cybersecurity firm
Check Point Research noted in a report shared with The Hacker News.
"Twenty four of the infected apps were aimed at children (ranging from puzzles to racing games), with the rest being utility apps (such as cooking apps, calculators, downloaders, translators, and so on)," the researchers said.
While the offending apps have been removed from Google Play, the find by Check Point Research is the latest in an avalanche of ad fraud schemes that have plagued the app storefront in recent years, with malware posing as optimizer and utility apps to perform phony clicks on ads.
Malware Abuses MotionEvent API to Simulate User Clicks
Stating that the campaign cloned legitimate popular apps to gain an audience, the newly discovered 56 apps
were found bypassing Google Play Store protections by obfuscating its native code and relying on Android's MotionEvent API to simulate user clicks.
Once an unwitting user installed one of the malicious apps, the Tekya malware registers a receiver, an Android component that's invoked when
a certain system or application event occurs — such as a device restart or when the user is actively using the phone.